The record-vying distributed denial-of-service attacks keep coming, with two mitigation services reporting they encountered some of the biggest data bombardments ever by threat actors whose tactics and techniques are constantly evolving.
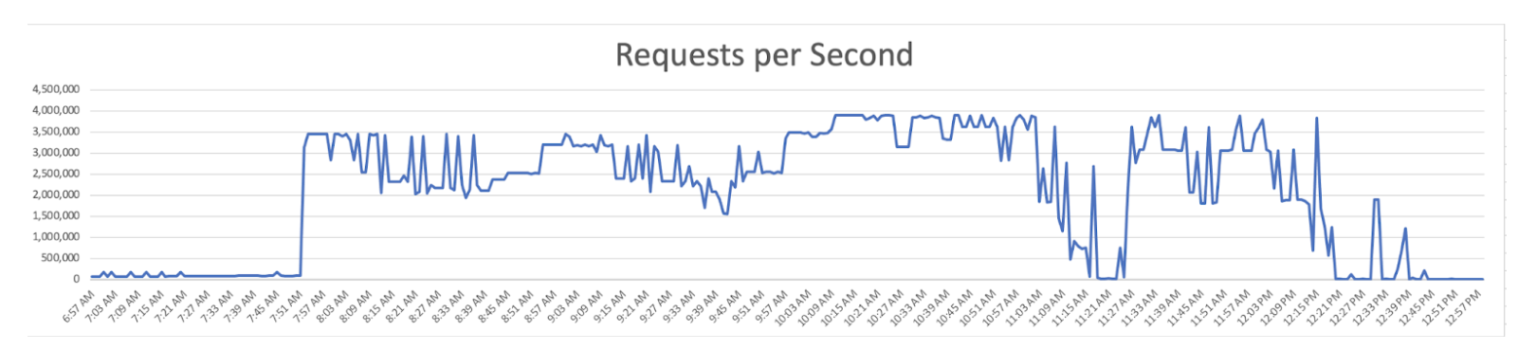
On Monday, Imperva said it defended a customer against an attack that lasted more than four hours and peaked at more than 3.9 million requests per second (RPS).
In all, the attackers directed 25.3 billion requests at the target with an average rate of 1.8 million RPS. While DDoSes exceeding 1 million RPS are growing increasingly common, they typically come in shorter bursts that measure in seconds or a few minutes at most.
A massive botnet
"[The] attackers used HTTP/2 multiplexing, or combining multiple packets into one, to send multiple requests at once over individual connections," Imperva's Gabi Stapel wrote. "This technique can bring servers down using a limited number of resources, and such attacks are extremely difficult to detect."
Stapel said that the attack likely would have peaked at an even higher rate had it not been countered by Akamai's mitigation service. The target of the DDoS was a Chinese telecommunications company that has come under attack before.
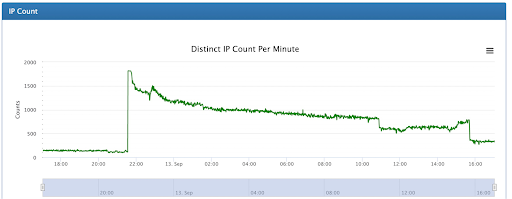
The attack originated with a botnet of routers, security cameras, and hacked servers connected to almost 170,000 different IP addresses. The IP addresses were located in more than 180 countries, with the US, Indonesia, and Brazil being the most common. Some of the botnet devices were hosted on various public clouds, including those offered by security service providers.


 Loading comments...
Loading comments...
