The Meeting Owl Pro is a videoconference device with an array of cameras and microphones that captures 360-degree video and audio and automatically focuses on whoever is speaking to make meetings more dynamic and inclusive. The consoles, which are slightly taller than an Amazon Alexa and bear the likeness of a tree owl, are widely used by state and local governments, colleges, and law firms.
A recently published security analysis has concluded the devices pose an unacceptable risk to the networks they connect to and the personal information of those who register and administer them. The litany of weaknesses includes:
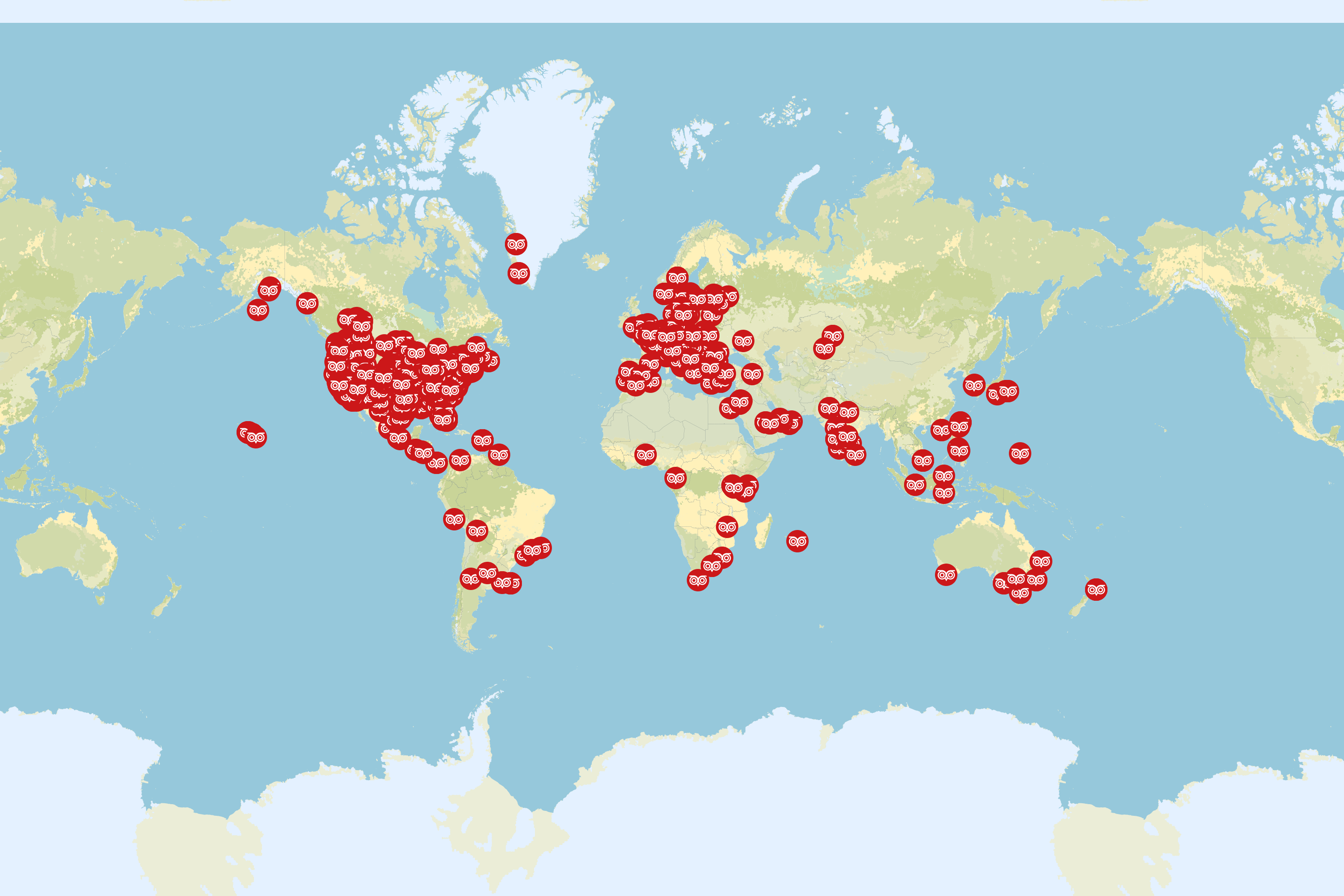
- The exposure of names, email addresses, IP addresses, and geographic locations of all Meeting Owl Pro users in an online database that can be accessed by anyone with knowledge of how the system works. This data can be exploited to map network topologies or socially engineer or dox employees.
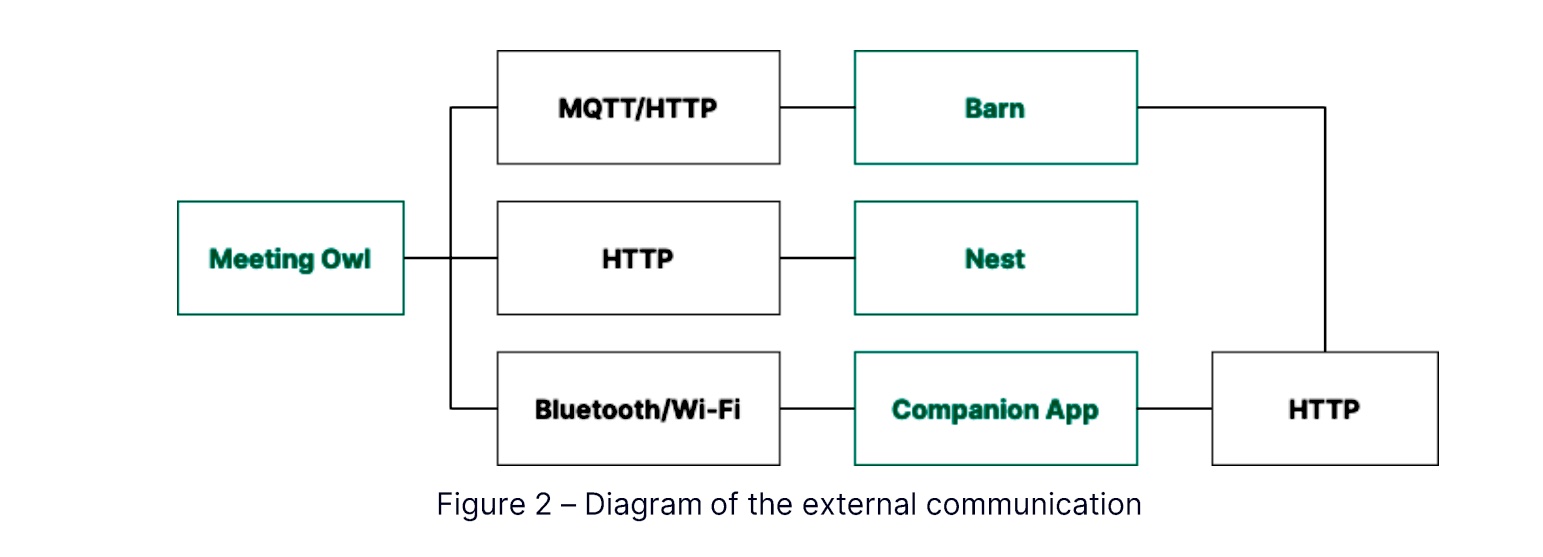
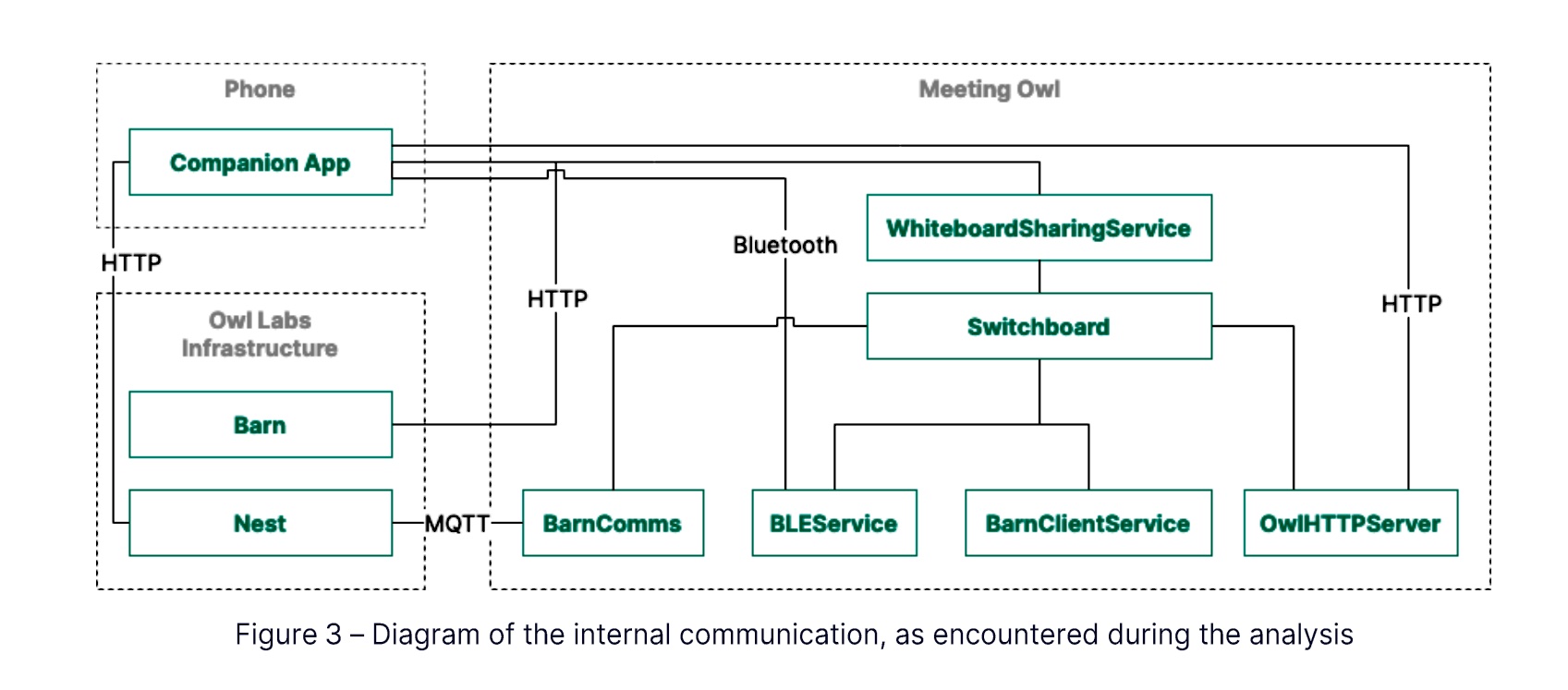
- The device provides anyone with access to it with the interprocess communication channel, or IPC, it uses to interact with other devices on the network. This information can be exploited by malicious insiders or hackers who exploit some of the vulnerabilities found during the analysis
- Bluetooth functionality designed to extend the range of devices and provide remote control by default uses no passcode, making it possible for a hacker in proximity to control the devices. Even when a passcode is optionally set, the hacker can disable it without first having to supply it.
- An access point mode that creates a new Wi-Fi SSID while using a separate SSID to stay connected to the organization network. By exploiting Wi-Fi or Bluetooth functionalities, an attacker can compromise the Meeting Owl Pro device and then use it as a rogue access point that infiltrates or exfiltrates data or malware into or out of the network.
- Images of captured whiteboard sessions—which are supposed to be available only to meeting participants—could be downloaded by anyone with an understanding of how the system works.





 Loading comments...
Loading comments...
